Information Technology
This site provides information, training, and support on computer hardware, software and services at Nicholls State University. You will find answers to most of the common problems people encounter while using campus computers, as well as lots of specialized information.
ACADEMIC COMPUTING
Mission
- Academic Computing supports the mission of the University by providing student and faculty services that assist with all technological aspects of learning in a University environment.
Functions
- Management of the University Learning Management System (Canvas)
- Management of the University email for students (GMail)
- Providing highly available computer labs for students, and assistance for faculty to integrate course materials into the curriculum.
- Ongoing procedural and educational training of students and faculty.
- Provide accountability to University and State Auditors, the SGA, and to the University Louisiana System board.
- Management and technical support of the compressed video network and VBrick streaming video systems.
- Provide computing resources to the faculty.
Implementation
- The managed labs allow students to complete reports and research necessary for course requirements. We have professional staff and trained students available to assist faculty and students in using University computing resources and multimedia classrooms.
- The technical support of the compressed video network is accomplished by working closely with office of Distance Education.
- Assessing Faculty and Student Computing needs.
- Academic Computing hosts web services for the department’s interactive pages.
| Building/Rm | Comments | Dept | Macs | PC |
| Peltier 120 | L&Lit Writing Comp Lab | Languages & Lit | 26 | |
| Peltier 131 | L&Lit Writing Comp Lab | Languages & Lit | 26 | |
| Peltier 165/166 | Student Help & Training Lab | Dyslexia Lab | 5 | |
| Peltier 206 | L&Lit Writing Forgien Lang. Lab | Languages & Lit | 26 | |
| Polk 125 | Student Help & Training Lab | Teacher Ed Lab | 2 | |
| Polk 142 | Student Teacher Lab | Teacher Ed Lab | 14 | 14 |
| Polk 137 LRC | Students Learning/Training on WhiteBds | COE | 1 | 21 |
| Polk 262 Psyc Lab | PSYC Lab | PSYC Lab | 4 | |
| Talbot 102 | MACO Student Use Mini Lab | Maco Stud Macs | 2 | |
| Talbot 103 | MACO Lab | Maco Lab | 19 | |
| Talbot 104 | MACO Radio Station | Maco Lab | 5 | |
| Talbot 106 | MACO MultiMedia Convergence Lab | Maco Lab | 17 | |
| Talbot 107 | MACO TV Studio Video Editing Lab | Maco TV Lab | 19 | |
| Talbot 204 | Art – Photograph Lab | Art Photography | 10 | |
| Talbot 207-A | Art – LU Lab | LU Lab | 2 | |
| Talbot 208 | Art – Graphics Art Lab | Art Adv. Graphics | 14 | |
| Talbot 211 | Music Lab w/ Notation & Marching Band | Music Lab | 18 | |
| Talbot TBD | Student Publications Lab (Nicholls Worth Mag) | NW, Ads, LP | 20 |
| Building/Rm | Comments | Dept | Macs | PCs |
| Ellender Library | Student Use | Open Lab (Floor) | 16 | 18 |
Technology Fee submission instructions and explanation of Student Subcommittee scoring:
Fee Definition and Authority
The Student Technology Fee (Tech Fee) is governed by Act no. 1450 of the regular session and is under supervision by each institution in higher education. This fee is considered a supplement to current funds allocated by the University and by grants. In October of 2012, the Nicholls State University Student Government Association voted unanimous approval for the assessment of a technology fee of $5.00 per credit hour, up to a maximum of $100.00 per semester, effective in the Fall 2013 semester. In a memorandum dated July 19, 1999, Mr. Bobby Jindal clarified fee expenditure guidelines that went into effect September 1, 1999. All Tech Fee requests must follow these guidelines.
Committee Makeup
Complying with guidelines issued by Mr. Jindal on July 19, 1999, the Student Technology Fee Committee is comprised of nine (9) students and eight (8) faculty/staff members giving the students a majority. Student makeup is composed of the Student Government Association President (or designee) and Vice President, one (1) student from each college, for a total of five (5), and two (2) students at large appointed by the SGA President. The faculty/staff makeup is composed of one (1) faculty member from each college, for a total of five (5), one (1) from the library, one (1) from Student Affairs, and one (1) from Student Life. The ex-officio members that do not have voting privileges include: Director of Academic Computing, Chief Information Officer, Member of University Administration, and all Instructional Technology Specialists and Computer Specialists from Academic Computing.
Scoring of Proposals
Points are given for each section and represent a weighted average. Sections with higher point totals indicate sections that are given greater consideration. Proposals are scored on a cumulative basis and are ranked by the total cumulative score. Those proposals ranking highest have the highest chance of being undertaken. The overall constraint is the amount of budget available for projects. In the event of a tie and only one project can be undertaken, the Tech Fee Committee will determine who shall get funded.
Procedure for Funding
As per Mr. Jindal’s guidelines, Nicholls State University has instituted a Student Technology Fee Plan. Line items inserted into the fee plan are composed of proposals from university colleges, from departments, and from the students.
The committee is first required to pass an overall budget that outlines the major categories of expenditures. In lieu of a Technical Review Committee, Academic Computing serves in this capacity and ranks the technical merit of each proposal and determines whether it fits into the overall plan for technology at Nicholls State University. If a proposal fits the description of technology, Academic Computing determines whether it is technically sound and whether human resources are available to implement and maintain all current production.
After the technical review is complete, the proposals are then submitted to the Student Technology Fee Subcommittee for consideration. The subcommittee scoring process usually takes place in late October, early November. The subcommittee makes their recommendations to the full committee where a vote is held to decide which proposals will get funded and for what amount. Upon approval by the full committee, the proposal is inserted as a line item into the Student Technology Fee Plan. Normally in December, after the vote, the proposal’s originator will receive a notification stating the outcome of the proposal. Minutes of these meetings are kept, which detail the discussion and debates on specific items and of the budget.
Presentation
The subcommittee may request the applicant to give a 5-minute presentation to further explain their proposal. The applicant will be contacted by Information Technology if a presentation is required.
Proposal Submission Instructions
Applicants must complete the online proposal located at the following link:
Student Technology Fee Proposal
To complete the Student Technology Fee Proposal, all quotes and sources of pricing must be attached to the proposal through the online forms system. Quote documents CANNOT be screenshots of website shopping carts. Proposal items should be sought from State-contracted companies first. If your proposal includes specialty items specific to your department (science, band, art, culinary, etc. equipment) please make sure your vendor is reputable and takes payment in the form of a purchase order.
In addition, applicants must complete the Budget Information document located at the following link.
Student Technology Fee Grant Proposal Budget Information
We recommend downloading the Budget Information document to your computer, filling it out in a PDF reader software (like Adobe Acrobat) before attaching it to the online form. Filling out the form in your web browser may have adverse side effects.
The completed online proposal including Department Head and Deans approvals must be submitted through the Online Forms system NLT 2:00 PM on the second Friday in October. Additional supporting documents should be attached to the online submission that include any quotes and/or sources of pricing generated while working on the proposal, especially for specialty items. Additionally, a proposal which includes a shopping list of individual items needs to be prioritized, in case funds cannot cover the entire proposal.
Rewarding of Winning Proposals
The money to purchase items awarded is from the current fiscal year’s budget; all attempts will be made to purchase prior to the June 30th purchasing deadline. However, projects funded should not anticipate delivery or completion prior to the start of the next semester. Academic Computing will set up a priority and distribution schedule. Completing all projects prior to the beginning of the Spring semester is impossible, as this does not give the staff of Academic Computing the necessary time to order, set-up, and test the equipment along with other time sensitive jobs already scheduled during that time. If these items are needed in a sensitive timeframe, please discuss with Academic Computing before the end of the semester to determine if it would be possible to be added to the schedule.
Inventory of Awarded Items
Items purchased for funded proposals will become the responsibility of the Department or College of the proposal. These items will be transferred to the appropriate inventory and any repairs after the end of the warranty period will be the responsibility of the Department or College. However, these items funded with Student Technology Fees must continue to adhere to the State’s Technology Fee guidelines, as they must be accessible for student use and must not be placed in faculty or staff offices.
How to Print to a Kiosk
Register with WEPA
Nicholls Students: WEPA accounts are automatically created and associated with your myNicholls ID and password. You will login with your same credentials as myNicholls and Moodle .
Other Users: Before printing to a WEPA kiosk, register at wepanow.com. You can also register directly at a kiosk by touching the Register Here button.
*A WEPA account is not required if using a USB drive to print directly from an kiosk.
Print to the WEPA Cloud
Printing from your personal computer: Download the WEPA print drivers from the WEPA website. Then, click the Print button in your application, select the WEPA printer (WEPA B/W or WEPA Color), and go to a WEPA Kiosk to pick up and pay. All WEPA printing on your computer goes to your WEPA account – keep this in mind if a friend uses your computer.
Printing from a Nicholls computer lab: Most Nicholls computer labs have WEPA print drivers installed, which allows you to select WEPA as the printer. In these labs, click the Print button in your application, select the WEPA printer (WEPA B/W or WEPA Color), enter your WEPA username and password, and go to a WEPA Kiosk to pick up and pay.
Printing using a USB drive at a WEPA kiosk: Press the “Print from a USB” option and insert a USB drive containing your files into the WEPA print kiosk and follow the on-screen instructions.
Printing from anywhere else: You can still print by uploading documents into your online WEPA account. This option works with a limited number of file types including Word, Excel, PowerPoint, and PDF. File size cannot exceed 20 MB.
Release a Print Job
Release Code: After you print from your computer, WEPA will give you a 6 digit release code. You can press the “Release Code” on the screen and you will be directed to that single print job. Select the print job and then select your payment option
Userid Login: After you have printed several jobs, you can print all of them at once by logging into your account at the Kiosk and hitting the “Select All” option, and then by selecting your payment option WEPA will print all of the selected jobs.
 Here are a few instructional videos about using the WEPA printing kiosks found around campus to print documents. More information about WEPA can be found at www.wepanow.com.
Here are a few instructional videos about using the WEPA printing kiosks found around campus to print documents. More information about WEPA can be found at www.wepanow.com.
How to print from a USB thumb drive
How to register for a WEPA Account at a kiosk
How to log in to your WEPA Account at a kiosk
How to login on www.wepanow.com to download computer print drivers
Direct Print Option
How to use a WEPA release code at a kiosk
Nicholls State University is now using WEPA as your campus printing solution. WEPA is a flexible solution for printing and offers a much higher quality output. WEPA offers the following advantages:
Accessibility
You can now print from the following locations:
- Brady Clubhouse – Lobby area, 1st floor
- Donald G. Bollinger Memorial Student Union
- Ellender Hall Dorm – Study Lab, 1st Floor
- Ellender Memorial Library – Room 125
- Ellender Memorial Library – Room 244
- Peltier Hall – Outside Room 101 (Auditorium)
- Polk Hall – 1st floor, LRC lab/Room 131
- Powell Hall – Room 109
Quality
The WEPA system uses a high quality paper and produces outstanding print quality.
Mobile Printing
You can now send email and attachments to any WĒPA™ kiosk. Whether you are using the iPhone, Android, or Blackberry you can download the WĒPA™ “app” from app member’s page and send documents to any WĒPA™ kiosk.
Coupons and More
Nicholls will be able to solicit vendor coupons and have them printed on the Kiosks at no charge to the students.
Convenience
Use your Colonel Card or Credit/Debit card.
TELECOMM & NETWORKING

To connect to the wireless network you will need to have the following items and settings:
- 802.11b/g/n/ac compliant wireless card
- Network type: Infrastructure
- SSID: NSUnwired
- Encryption: off
- TCP/IP settings: DHCP
Please note:
NSUnwired is for student, faculty, staff, and guest access.
802.11a/b/g/n/ac compliant wireless card
You will need an 802.11a/b/g/n/ac compliant card. When purchasing a wireless card, make sure the card is compliant or certified. Some wireless cards are 802.11a only, 802.11b only, 802.11g only, 802.11n only, or 802.11ac only, and some cards are a combination of the standards. If at all possible, choose a card that supports a combination of the three latest standards of 80.11b/g/n/ac. A wireless card that supports all standards will work in all wireless locations on campus. In addition, make sure that you install the latest drivers for compatibility
and to resolve any issues. Visit the manufacturer’s web site for information about obtaining the latest drivers.
The Wi-Fi Alliance is a nonprofit international association that certifies wireless products based on the IEEE 802.11 standard. Visit their web site at www.wi-fi.org to find out if your wireless adapter has been certified.
Network Type: Infrastructure
802.11 defines two types of network: infrastructure and ad hoc. An infrastructure type indicates that your wireless client will connect to the wired network via an access point. Ad Hoc, on the other hand, indicates a type of network where only wireless clients get to communicate among each other. You must use infrastructure in order to connect to the Nicholls wireless network.
SSID: NSUnwired
SSID stands for Service Set IDentifier, sometimes referred to as Network Name. This is simply a name used to identify a wireless network. An SSID can either be broadcast or hidden. When the SSID is hidden, the user must know what the SSID of the wireless network is in order to gain access. When the SSID is broadcast, the wireless network is available to anybody. The access points on the Nicholls wireless network are configured to broadcast their SSID. While on campus, if your wireless device says that it has found a “New Wireless Network NSUnwired, Would You Like to Connect?”, go ahead and connect. Some wireless adapters will allow you to leave the SSID field blank or enter the word “ANY”. This instructs the wireless clients to obtain whatever SSID is being broadcast by the access point. You can also set the SSID explicitly. If your wireless device fails to auto-detect “NSUnwired” and connect to the Nicholls wireless network, you can enter NSUnwired into the SSID field.
Encryption: off
The 802.11 standard makes use of optional security mechanisms called WEP (Wired Equivalent Privacy) or WPA (Wi-Fi Protected Access). Make sure encryption is turned off.
TCP/IP settings: DHCP
There are two ways of assigning an IP address to a network adapter: static or DHCP. Static assignment requires the use of a unique IP address that will only work on a particular subnet and must be entered manually. DHCP (Dynamic Host Configuration Protocol) on the other hand, refers to the automatic assignment of an IP address. No user intervention is required. The only thing the user is responsible for is to set the TCP/IP settings on the network adapter to DHCP.
Check the list below to see which specific indoor and outdoor areas have wireless coverage.
Wireless Coverage By Building
| Building | Location within Building | Standard |
| Ayo Hall | Full Coverage | 802.11 A/G/N |
| Beauregard | Full Coverage | 802.11 A/G/N |
| Candies | Full Coverage | 802.11 A/G/N |
| Calecas | Full Coverage | 802.11 A/G/N/AC |
| Century Club | Full Coverage | 802.11 A/G/N/AC |
| Culinary | Full Coverage | 802.11 A/G/N |
| Elkins Hall | Full Coverage | 802.11 A/G/N |
| Gouaux Hall | Full Coverage | 802.11 A/G/N |
| Ledet | Full Coverage | 802.11 A/G/N/AC |
| Library 1st Floor | Full Coverage | 802.11 A/G/N/AC |
| Library 2nd Floor | Full Coverage | 802.11 A/G/N/AC |
| Library 3rd Floor | Full Coverage | 802.11 A/G/N/AC |
| Millet | Full Coverage | 802.11 A/G/N |
| Peltier Hall | Full Coverage | 802.11 A/G/N/AC |
| Picciola Hall | Full Coverage | 802.11 A/G/N |
| Polk Hall | Full Coverage | 802.11 A/G/N/AC |
| Powell Hall | Full Coverage | 802.11 A/G/N |
| Scholars | Full Coverage | 802.11 A/G/N/AC |
| Shaver Gym | Full Coverage | 802.11 A/G/N |
| Student Union | Full Coverage | 802.11 A/G/N/AC |
| Student Union Ballroom | Full Coverage | 802.11 A/G/N/AC |
| Talbot | Full Coverage | 802.11 A/G/N/AC |
| White Hall | Full Coverage | 802.11 A/G/N |
| Zeringue | Full Coverage | 802.11 A/G/N |
Outdoor Coverage
| Outdoor | Standard |
| Quadrangle | 802.11 A/G/N |
| Student Union Outdoor Seating Area | 802.11 A/G/N |
| Library Entrance Area | 802.11 A/G/N |
| Talbot Hall Entrance Area | 802.11 A/G/N |
| Powel/White Hall Courtyard Area | 802.11 A/G/N |
| Baseball Field | 802.11 A/G/N |
| Football Stadium | 802.11 A/G/N |
Nicholls State University provides wireless internet connectivity for Academic and Residential computing. While not flawless, this service is reaching maturity and is seeing few failures due to service provisions.
Most often, wireless connectivity issues are not due to failed wireless services, but rather the user’s computers. This write-up will discuss several aspects of problematic wireless connectivity; after all, knowledge is power. This article is written for the end-user with MS-Windows based computers in mind; however, other operating system utilities may also be listed.
Low signal strength is often a reason for failed connectivity. Signal strength is often measured in “bars” for simplicity. Five (5) bars is an excellent signal strength and one (1) bar is a poor signal strength. You should be aware that you can still connect with 1 and 2 bars, however you may suffer from slow speeds and possible disconnects. 2 bars although low, will generally not have significant problems. Some computers allow boosting of the internal antenna’s power level. Doing so may allow for more bars. For instructions on this, please see this link.
When regarding wireless connectivity, terms like “Line-of-Sight”, “Barrier Interference”, and “Electrical Noise” have significant meaning. Line-of-Sight references a straight line between your computing device and the Access Point. It is always best to minimize the number of barriers between you and the Access Point. Barriers include walls and large objects especially metal objects, that may block or deflect wireless signal. Also, the electrical interference of other electronics such as blue tooth devices, phones, refrigerators, microwaves, and other computing devices can easily interfere with wireless connectivity quality.
Not all hardware providers use the best quality components. It is a simple fact that some built-in wireless adapters are inadequate. Purchasing and using a USB wireless adapter may in fact give you a much better connection than the built-in wireless adapter. Often changing from completely unable to connect situation to a 4 bar connection.
There are also tools available that can assist you with finding better signals. These are often called Wireless (or WiFi) Stumblers and Scanners. If you are an advanced user or are open to experiment, please Google this advanced topic. Stumblers written for Apple OSX often allow you to connect to specific signals found by the utility. OSX based stumblers include KisMac, AP Grapher, iStumbler, and Air Radar. Windows based stumblers tend to only display information, albeit very detailed information. Windows based stumblers include InSSIDer, Meraki, and NetStumbler. For Linux there is WiFi Radar and IWScanner.
One last wireless specific issue worth mentioning is regarding Ad-Hoc networks, which is basically other computers advertising wireless signals which are not internet Access Points. A big issue found recently is called Viral SSID’s. This is a host of computers pretending to be Access Points in lure of unsuspecting users to connect to them. Once connected, the user’s computer becomes one of the culprits, thus the term “Viral”, providing persistent advertisements of fake internet services. Users should follow these instructions to delete or disable Ad-Hoc connections. Do not connect to “HP Setup” nor “Free Public WiFi”.
Another big issue with computers is due to malicious software. Malware, as it is called, can be the culprit of a wide range of computer problems including slowness, crashes, information theft and even network connectivity problems. Often, especially with windows based computers, failing connectivity is due to Malware and excessive background processes.
In regards to Malware, there are quite a few cleaning utilities available. One of the most-recommended and free for personal use, is a utility called Malware Byte’s Anti-Malware. The free utility will not keep your computer protected in real-time, but it is among the best on-demand cleaners available. It will scan for and clean a vast number of malicious software.
It is also recommended that your Anti-Virus be fully functional and updated for real-time protection. No single anti-virus is 100% effective; however, they do provide a high level of protection. There are several free Antivirus and software suites available. Among the most popular providers are Avast, AVG, PCTools, BitDefender, Comodo, and Panda. When installing one of these products, it is prerequisite to uninstall the existing antivirus.
If your computer is known to be infected, SmitFraudFix may resolve some persistently odd infection issues.
Peer to Peer (P2P) applications, for example, Torrent Clients, etc. are known to diminish both the user’s internet connection and neighbors’ internet connections. Using these software applications for downloading and sharing files will significantly slow your connection and also slow the connections of others connected to the same access point. Please refrain from using P2P applications.
I. PURPOSE
The effective management of information technology resources is crucially important to the success of the mission of Nicholls State University. Because of the inherent insecure nature of wireless communication, wireless networks require increased cooperation and coordination between campus entities to maximize the technology’s benefits to the students, faculty, and staff of the University, to allow connection to wireless networks in different campus buildings, and eventually, to facilitate the ability to roam from building to building without losing network connectivity. This document sets forth the policies for using wireless technologies and assigns responsibilities for the deployment of wireless services and the administration of the wireless radio frequency spectrum in a distributed campus network environment. This policy expands the University Computer Use Policy and the Student Computer Use Policy by including specific direction regarding wireless communications and the resolution of issues that may arise. This policy is subject to change as new technologies and processes emerge.
II. REFERENCES
Student User Agreement Form
Student Wireless Access Form
Student Computer Use Policy
Electronic Email Policy
Lab and Network Usage Policy
University Computer Use Policy
III. DEFINITIONS
Wireless Network means local area network technology that uses radio frequency spectrum to connect computing devices to college, department, or division wired networks and may connect to the Campus Network Backbone and the Internet.
Access Point means electronic hardware that serves as a common connection point for devices in a wireless network. An access point acts as a network hub that is used to connect segments of a LAN, using transmit and receive antennas instead of ports for access by multiple users of the wireless network. Access points are shared bandwidth devices and can be connected to the wired network, allowing access to the campus network backbone.
Wireless Infrastructure means wireless access points, antennas, cabling, power, and network hardware associated with the deployment of a wireless communications network.
Coverage means the geographical area where a baseline level of wireless connection service quality is attainable.
Interference means the degradation of a wireless communication signal caused by electromagnetic radiation from another source. Interference can slow down or eliminate a wireless transmission depending on the strength of the interfering signal.
Privacy means the condition that provides for the confidentiality of personal, student, faculty and staff communications, and institutional data transmitted over a wireless network.
Client hardware/software means the electronic equipment and software that is installed in a desktop, laptop, handheld, portable, or other computing device to provide a LAN interface to a wireless network.
IV. SCOPE
This policy applies to all wireless network devices utilizing Nicholls State University IP space (including private IP space within University networks) and all users of such devices, and governs all wireless connections to the campus network backbone, frequency allocation, network assignment, registration in the Domain Name System, and services provided over wireless connections to the campus network backbone to colleges, departments, or divisions of Nicholls State University.
V. AUTHORITY
This policy is under the authority and oversight of The Division of Information Technology including the Department of Academic Computing under the direction of the Executive Vice President. Technical review of this document is under the direction and authority of The Division of Information Technology including the Department of Academic Computing under the direction of the Executive Vice President.
VI. POLICY
Wireless equipment and users must follow all network connection policies as set forth in the University Computer Use Policy and the Student Computer Use policy. All provisions of the ISO Minimal Security Requirements and Practices apply to this policy.
Interference or disruption of other authorized communications that result from the intentional or incidental misuse or misapplication of wireless network radio frequency spectrum is prohibited.
Wireless access points must abide by all federal, state, and local laws, rules or regulations pertaining to wireless networks.
Deployment and management of wireless access points is the responsibility of The Division of Information Technology as under the direction of Executive Vice President.
University colleges, departments, or divisions must register for the use of radio frequency spectrum with The Division of Information Technology including the Department of Academic Computing , prior to implementation of wireless networks.
The location of all wireless access points must be registered with the The Division of Information Technology.
Wireless access points shall require user authentication at the access point before granting access to campus or Internet services. Wireless network interfaces and end-user devices shall support authentication to access wireless networks that allow connectivity to the Campus Network Backbone.
Physical security should be considered when planning the location of wireless access point and other wireless network components.
Wireless networks must be designed and deployed to avoid physical and logical interference between components of different network segments and other equipment. In the event that a wireless device interferes with other equipment, The Division of Information Technology shall resolve the interference as determined by use priority.
The Division of Information Technology including the Department of Academic Computing will attempt to resolve any interference or security incidents by coordinating with the registered Point of Contact (POC) for the wireless network. If a POC is not available, the incident is resolved through administration of the network connection to the backbone.
The Division of Information Technology including the Department of Academic Computing is authorized to take whatever reasonable steps are necessary to ensure compliance with this, and other network related policies that are designed to protect the integrity and security of the campus network backbone.
Disconnect Authorization – Any wireless network on campus, which poses a security threat, may be disconnected from the campus backbone network. If a serious security breach is in process, The Division of Information Technology including the Department of Academic Computing may disconnect the LAN immediately. Every reasonable attempt will be made to reach the registered “Point of Contact” to resolve security problems. The Division of Information Technology has the authority to disconnect any wireless network from the campus network backbone whose traffic violates practices set forth in this policy, or any network related policy. It is the responsibility of the college, department, or division to be knowledgeable regarding the provision such policies.
Grievance matters with this policy or conflicts between The Division of Information Technology including the Department of Academic Computing and any University college, department, or student are directed to the Executive Vice President for resolution.
There are no guarantees that all brands of wireless networking equipment will work on the Nicholls State University network. Currently the only accepted standard is 802.11a, b, and g. These standards are subject to change as new technologies and standards evolve. Please check with The Division of Information Technology including the Department of Academic Computing as to the current recommendations.
Coverage is limited on campus and there are no guarantees to the amount of coverage on the campus.
INFORMATION TECHNOLOGY STAFF
| Name | Title | Phone Number |
|---|---|---|
| Sam Cagle | Chief Information Officer | 985-448-4408 |
| Randy LeBlanc | Administrative Program Specialist A | 985-448-4419 |
Academic Computing
| Name | Title | Phone Number |
|---|---|---|
| Perry Lawless | Director, Academic Computing | 985-448-4417 |
| Nik Dronet | IT Systems Architect | 985-448-4439 |
| Ryan Dubina | IT System Administrator LMS | 985-448-4978 |
| Jacob Frey | IT Client Support Specialist | 985-448-4200 |
| Vacant | IT System Administrator Classroom Technology | 985-449-7126 |
| Keith Carroll | IT System Administrator Classroom Technology | 985-448-4220 |
| Leah Lirette | IT Client Support Specialist for Student Support | 985-448-4413 |
Enterprise Information Systems
| Name | Title | Phone Number |
|---|---|---|
| Stacey Latka | Director, Enterprise Information Systems | 985-448-4414 |
| Claire Shaw | Information Equipment Operator 3 | 985-448-4410 |
| Darren Adams | IT Senior Systems Programmer | 985-448-4412 |
| Tim Authement | IT Senior Programmer Analyst | 985-448-4940 |
| Adam Lamartina | IT Systems Administrator | 985-449-7138 |
| Nick Hotard | IT Client Support Specialist | 985-449-7032 |
Networking and Telecommunications
| Name | Title | Phone Number |
|---|---|---|
| Slade Besson | Director, Telecomm and Networking | 985-449-7010 |
| Jared Domangue | Network Administrator | 985-449-7011 |
| Louis Caro | Telecom Coordinator | 985-448-4999 |
| Lucas LeCompte | Network Specialist | 985-449-7173 |
Security and Identity Management
| Name | Title | Phone Number |
|---|---|---|
| Chris Usey | IT Security and Identity Managment Engineer | 985-448-4409 |
| Reagan Daigle | IT System Administrator Identity Management | 985-448-4401 |
| Joe Bernard | IT Systems Administrator ID Card | 985-448-4967 |
POLICY & PROCEDURE
Nicholls State University maintains certain policies with regard to the use and security of its Information Technology (IT) resources, including computer usage, computer systems and networks. Nicholls State University IT policies exist to maintain, secure, and ensure legal and appropriate use of the university’s information technology infrastructure. Security and privacy policies work together to provide the campus community with a high quality, trusted, and secure campus computing environment. They also help protect and secure property interests, data, and intellectual property. All users of Nicholls State University’s IT resources and facilities are expected to be familiar with and adhere to the Nicholls State University IT policies and will be subjected to the consequences of and/or penalties for violating University policies. Nicholls State University’s IT Policies apply to the entire Nicholls community, including faculty, staff, and students. The full database of Nicholls State University can be found on our policy and procedure webpage, located at https://www.nicholls.edu/information-tech/policyandprocedure/
Password Reset Procedure
Various options are available to assist users with changing a forgotten or expired password. To make the process of resetting your password as smooth as possible, please make sure your personal information and security questions are always up to date in the Banner Self Service system.
myNicholls ID Password Reset Options:
Changing your myNicholls ID requires access to your Nicholls Google Email Account. If you are unable to login to your Google Account please see the Google Account Password Reset Options below.
To initiate a myNicholls ID password reset, navigate to the myNicholls ID password Self Service web page and follow the directions. You will need to provide your:
- myNicholls ID (ex: ctillou1)
- Your Nicholls Email Address
- Student Example: ctillou1@nicholls.edu
- Faculty Staff Example: colonel.tillou@nicholls.edu
Once the information is submitted, check your email and follow the instructions in the password reset email to reset your password.
Google Account Password Reset Options:
In the event you forget your Google Account Password you will need to contact IT support using one of the following methods below. Please be aware you will be asked to provide personal information in order to verify your identity.
In Person
If you are local to the Thibodaux, LA area, please visit the IT Department, located in Peltier Hall room 156 on the Nicholls’ campus. Present a valid identification card (must contain a photo), such as a driver’s license, state ID, Colonel Card, etc to verify your identity and a member of the staff will assist you with resetting your password.
Phone
If you are unable to visit in person you may request a password reset via phone at 1-985-448-4419. A staff member may ask you a number of personal questions to verify your identity. If you are able to successfully validate your identity the staff member will assist you with resetting your identity over the initial phone call. If you are unable to successfully answer all the validation questions the staff member may provide you with a temporary password to one of the email addresses or phone numbers on file.
Email/Fax
You may send a password reset request via email at itsupport@nicholls.edu or via FAX at +1 (985) 448-4421. Your request must contain:
- a copy of a valid photo identification card
- a signed note requesting your password reset, and
- an alternate email address or phone number where you can be contacted.
Once submitted, contact IT Support at +1 (985) 448-4419 to verify receipt of the fax and to reset your password.
BANNER 9
Oracle will soon be ending support for Oracle Forms 11gR2, which is utilized by our Banner 8 system. The upgrade delivers a number of important enhancements, including a modern user interface, enhanced navigation and process management tools, and new functionality across the student platform. It will also allow us to run Banner on any browser and on mobile devices. There is no need to learn a new application, just the new interface.
Benefits of Banner 9 |
|
![]() CLICK HERE TO DOWNLOAD PRINTABLE PDF
CLICK HERE TO DOWNLOAD PRINTABLE PDF
The following keyboard shortcuts have changed from Banner 8 to Banner 9:
| Action | Banner 8 | Banner 9 |
|---|---|---|
| More Information | ALT+H | CTRL+SHIFT+U |
| Next Block or Section | CTRL+Page Down | ALT+Page Down |
| Previous Block or Section | CTRL+Page Up | ALT+Page Up |
| Open Menu Directly | F5 | CTRL+M |
| Select on a Called Page | SHIFT+F3 | ALT+S |
| Rollback or Clear Page | SHIFT+F7 | F5 |
| SHIFT+F8 | CTRL+P |
The following keyboard shortcuts are new to Banner 9:
| Action | Banner 9 |
|---|---|
| Submit Workflow | ALT+W |
| Release Workflow | ALT+Q |
| Expand/Collapse a Drop-down Field | ALT+DOWN ARROW |
| Change MEP Context | ALT+SHIFT+C |
| Open Related Menu | ALT+SHIFT+R |
| Open Tools Menu | ALT+SHIFT+T |
| Last Page | CTRL+END |
| First Page | CTRL+HOME |
| Page Tab 1 Page Tab 2 and so on… | CTRL+SHIFT+1 CTRL+SHIFT+2 and so on… |
| Sign Out (Application Navigator) | CTRL+SHIFT+F |
| Display Recently Opened Pages (Application Navigator) | CTRL+SHIFT+L |
| Open Search (Application Navigator) | CTRL+SHIFT+Y |
| Toggle Accessibility Mode for current session | CTRL+B |
| Toggle Multi/Single Records View | CTRL+G |
| Open Help (Application Navigator) | CTRL+M |
| Open Menu (Application Navigator) | CTRL+Y |
| Export | SHIFT+F1 |
The following keyboard shortcuts remain the same from Banner 8 to Banner 9:
| Action | Banner 8 and 9 |
|---|---|
| Edit | CTRL+E |
| Cancel Page, Close Current Page, Cancel Search/Query, or Exit | CTRL+Q |
| Down/Next Record | DOWN ARROW |
| Choose/Submit | ENTER |
| Duplicate Item | F3 |
| Duplicate Selected Record | F4 |
| Insert/Create Record | F6 |
| Search/Open Filter Query | F7 |
| Execute Query | F8 |
| List Values | F9 |
| Save | F10 |
| Next Page Down | PAGE DOWN |
| Previous Page Up | PAGE UP |
| Count Query | SHIFT+F2 |
| Clear One Record | SHIFT+F4 |
| Clear All in Section | SHIFT+F5 |
| Delete Record | SHIFT+F6 |
| Previous Field/Item | SHIFT+TAB |
| Next Field/Item | TAB |
| Up/Previous Record | UP ARROW |
Bookmarks and Favorites
For quick access to Banner 9, please bookmark the myNicholls website. The myNicholls website is the central location for all Nicholls State University single sign-on compatible applications.
Query Mode Sticking
If you see a “query mode only” message in a Banner page you should be able to make entries to, try exiting to the menu. Accessing a page from another page often results in the restrictions or permissions from the initial page “following” you.
NOTE: You must be logged in to your @nicholls.edu Google account to view this video. You can login through YouTube.
ONLINE FORMS
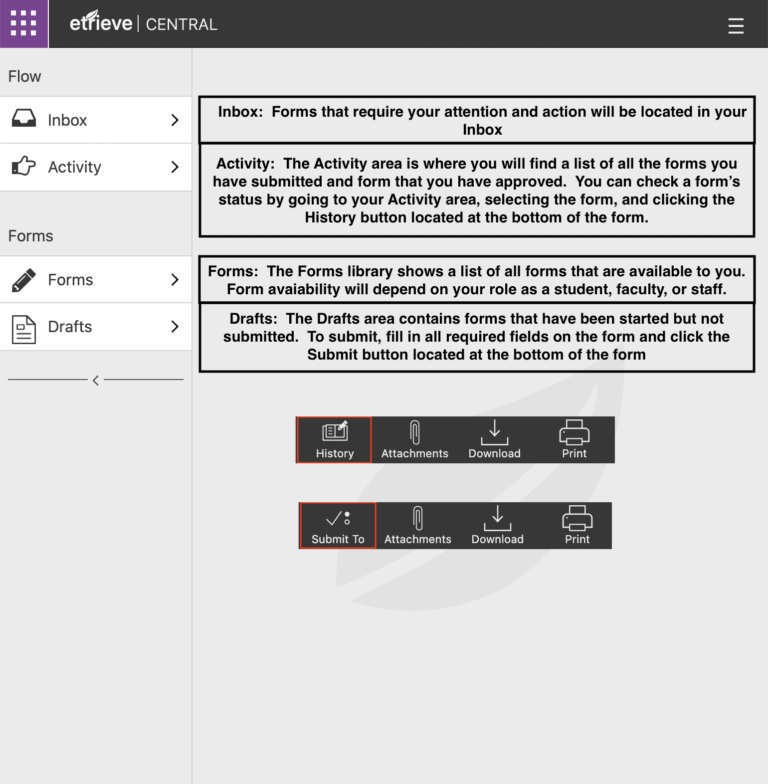
Etrieve is Nicholls State University’s Online Forms system designed to improve efficiency and accuracy for many of our campus processes.
The Etrieve Online Forms system is available through the my.nicholls.edu single sign-on page. Your login not only verifies your identity and acts as your digital signature, but also allows certain fields in the form to be pre-populated for convenience and accuracy.
When submitted, the form follows an established workflow notifying each person that has a role in the form’s completion that an action needs to be taken.
ONLINE SUPPORT
Student Support – Students may email itsupport@nicholls.edu or call 985-448-4400 for tech issues such as e-mail, Canvas, and account issues.
Online Helpdesk (Faculty/Staff) – Submit tickets for various technological issues. You may also request new user accounts and eQuotes. The Helpdesk website is only accessible on-campus by faculty and staff users.
myNicholls ID Password Self Service – Manage and change your myNicholls ID password.

